- Burp Suite Ntlm Authentication Code
- Ntlm V2 Authentication
- Burp Suite Windows Authentication
- Disable Ntlm Authentication
- Burp Suite Ntlm Authentication System
Complete suite for web application attacks: webcrawler, web vulnerability scan, web attacks.
Configure sqlmap with burp suite proxy NTLM Authentication Some web application needs NTLM authentication, especially.NET, and testing for SQL Injections becomes very important in such critical applications. In Backtrack, if we want to test for SQL Injection using SQLMap it needs 'python-NTLM' in order to test such applications. When an application is using NTLM authentication, you will need to configure Burp Suite to automatically carry out the authentication process. You can configure these settings at User Options Connections Platform Authentication. Use the Add function to configure new credentials.
- Burp session handling rules are very powerful. In this episode, we have seen an example of how to configure burp to auto login or activate session after it d.
- Burp Suite Free Edition and NTLM authentication in ASP.net applications 2 Replies As you know, Burp Suit is a scanner for advanced Web Application Security researchers. However, the free version of Burp is more like Firebug analogue, but much more functional.
- There is an internal application which authenticates based on windows credentials (NTLM Authentication). It is not intercepting while in proxy with Burp Suite and is stuck in login pop-up even after providing correct credentials. Upon removing the proxy, the application works fine.
Test behind a proxy (e.g. corporate network)
- Find proxy information from http://wpad/wpad.dat
- Click on 'User options' tab
- Under 'Upstream Proxy Servers', click Add
Credentials are NOT encrypted when stored by Burp. On Windows, they can be found at C:UsersAppDataRoamingBurpSuitebapps in the .json file.
Fix common errors
Fix: Pop-up windows not showing buttons (Burp 2020.1)
- Install Java 9 or later. Download Java.
- Or use JDK for launching the JAR.
- Or this can happen when not enough RAM.
Environment variable
In Control Panel/System/Advanced System Settings, add new system variable JRE_HOME:
Check Java version
Fix: A website with error in certificate can't connect to proxy
- Click on 'User options' tab
- Under 'Upstream Proxy Servers':
- Click Add
- Destination host: myserver
- Proxy host: (leave empty)
- Proxy port: (leave empty)
Fix: Connection is not secure / Install Burp's certificate
To use Burp proxy more effectively with HTTPS websites, install Burp's certificate. See Installing Burp's CA certificate.
Add Burp root certificate in Firefox
- Using Burp as proxy, go to http://burp/
- Click on CA Certificate and download the file
- In Firefox, click on Options -> Privacy & Security
- Under Security -> Certificates, click on View Certificates
- Click on Import and select Trust this CA to identify websites, email users and software developers
Authentication using certificates
Generate PKCS#12 file (.pfx or .p12)
TIP: You MUST specify a password when creating the PKCS#12 file because Burp requires a password.
Import certificate in Burp
- Click User options -> TLS
- Under Client TLS certificates, click Add
- Specify the host that requires the certificate
- Select File (PKCS#12)
- Choose the .p12 file and enter the password
Usage
Starting Burp Suite Pro using the jar file.
NTLM
To test using NTLM credentials, use
Burp Suite Ntlm Authentication Code
- Tab User options -> Platform Authentication
- Select Do platform authentication
- Enter Destination host, type: NTLMv2, username and domain
Burp Tabs
Dashboard
Web vulnerability scanner. Pro version only.
Target
Visualize the target application's contents in a folder structure hierarchy that corresponds to the site's URL. Shows all the content that has been discovered until now, by manually browsing the site's pages.
Target Scope
- Click on Target -> Scope
- Click on Use advanced scope control
- Under Include in scope, click on Add
- In Host or IP range, enter a regular expression
All subdomains of test.com
Hostname is exactly something.else.com (no /something)
Hostname is exactly something.else.com + something.else.com/…
Generate report
Never send this report as is to a client, always look for false positive before sending.
Proxy
Main engine of Burp, which allows it to intercept and modify all web traffic.
Intruder
Carry out automated, customized attacks against web applications. Web fuzzing (send unexpected input to target application). This process may help to identify web application security flaws.
Repeater
Manually modify and reissue web requests.
Ntlm V2 Authentication
Sequencer
Analyzes the quality of randomness in an application's session tokens or other important data items that are intended to be unpredictable.
Decoder
Burp Suite Windows Authentication
Allows for encoding and decoding data.
Comparer
Utility to perform visual diff between any two items of data, such as similar web responses.
Disable Ntlm Authentication
Extender (PRO ONLY)
'BApp Store' allows you to load Burp extensions, which extend Burp's functionalities through using third-party apps.
Project Options
User Options
Burp Suite Ntlm Authentication System
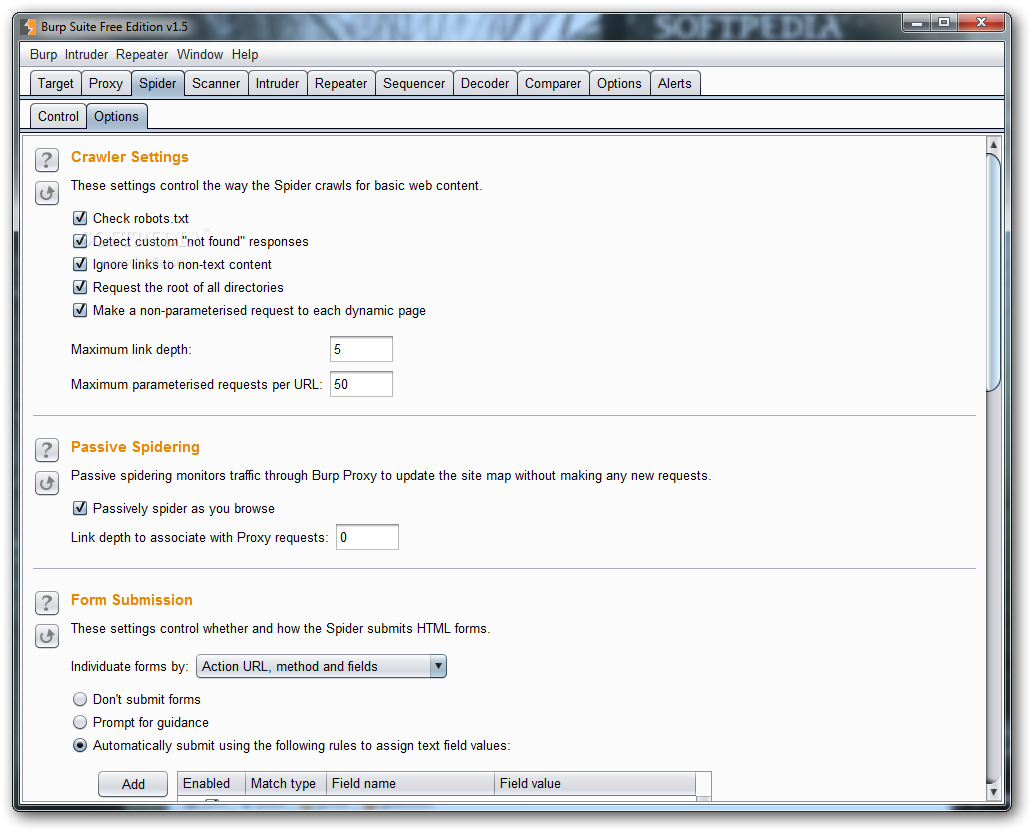
SPIDER (DEPRECATED)
Crawls applications to locate contents and functionalities.